TLS - SSL #
Problem #
- If a website uses HTTP without SSL/TLS, all packets sent over the internet can easily be captured and read (see packet sniffing demonstration)
- How can a user determine if the website they are currently visiting is the original or a look-alike website created by a hacker to impersonate it? (see dns poisoning demonstration)
Overview #
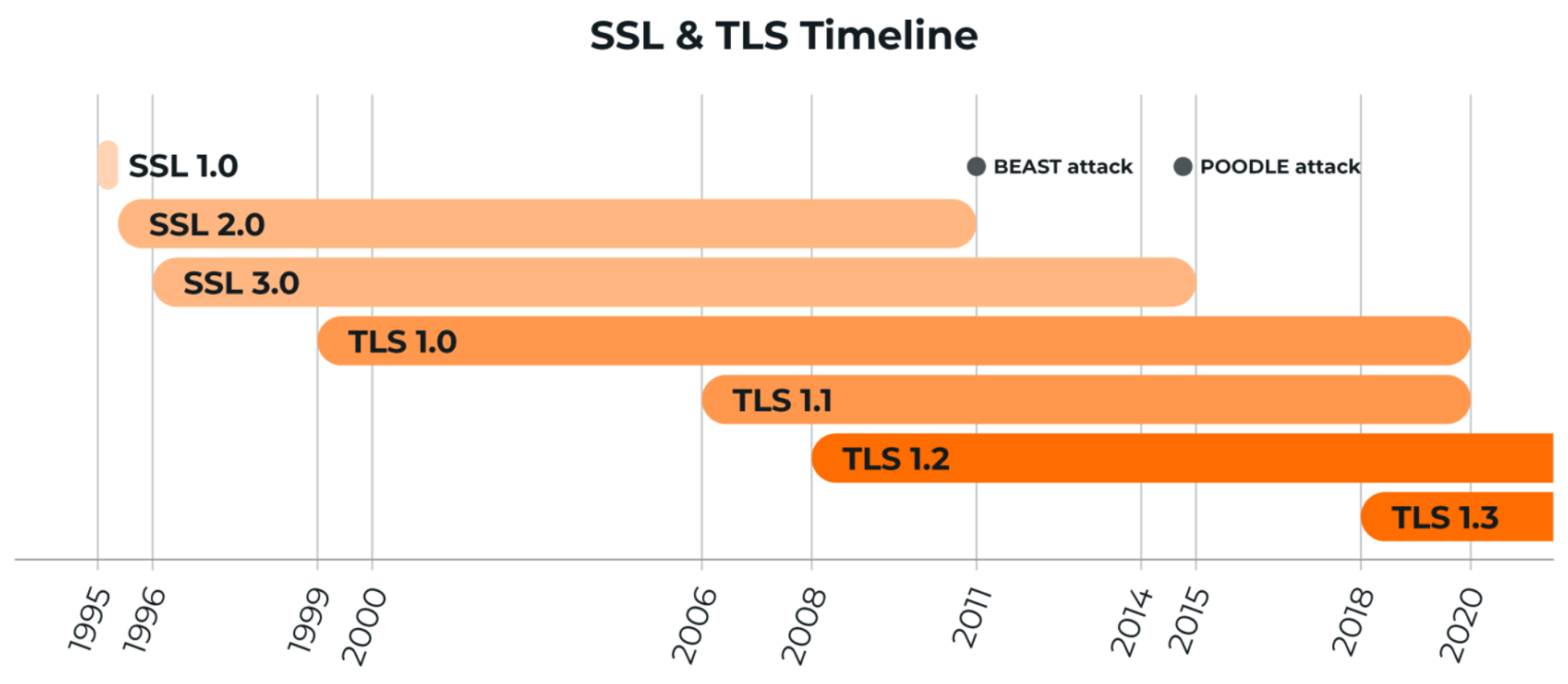
- The internet’s official birthday is January 1, 1983
- A protocol for encrypting, securing, and authenticating communications that take place on the Internet
- SSL was replaced by an updated protocol called TLS some time ago, SSL is still a commonly used term for this technology
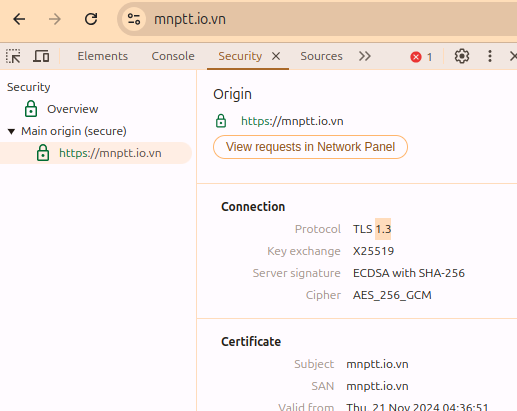
- To see which TLS version of a website (on Chrome):
- Open the Developer Tools (Ctrl+Shift+I)
- Select the Security tab
- Navigate to the Origin you want to inspect
- At the Connection section, check the results which TLS protocol is used
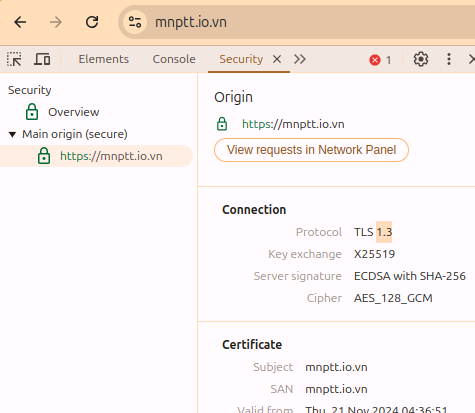
TLS 1.2 #
- Key exchange algorithm: Utilize the encryption and decryption capabilities of asymmetric encryption
- Round trip time: 2 RTT
- Compatibility: Supported by both older and newer versions of all browsers
Flow #
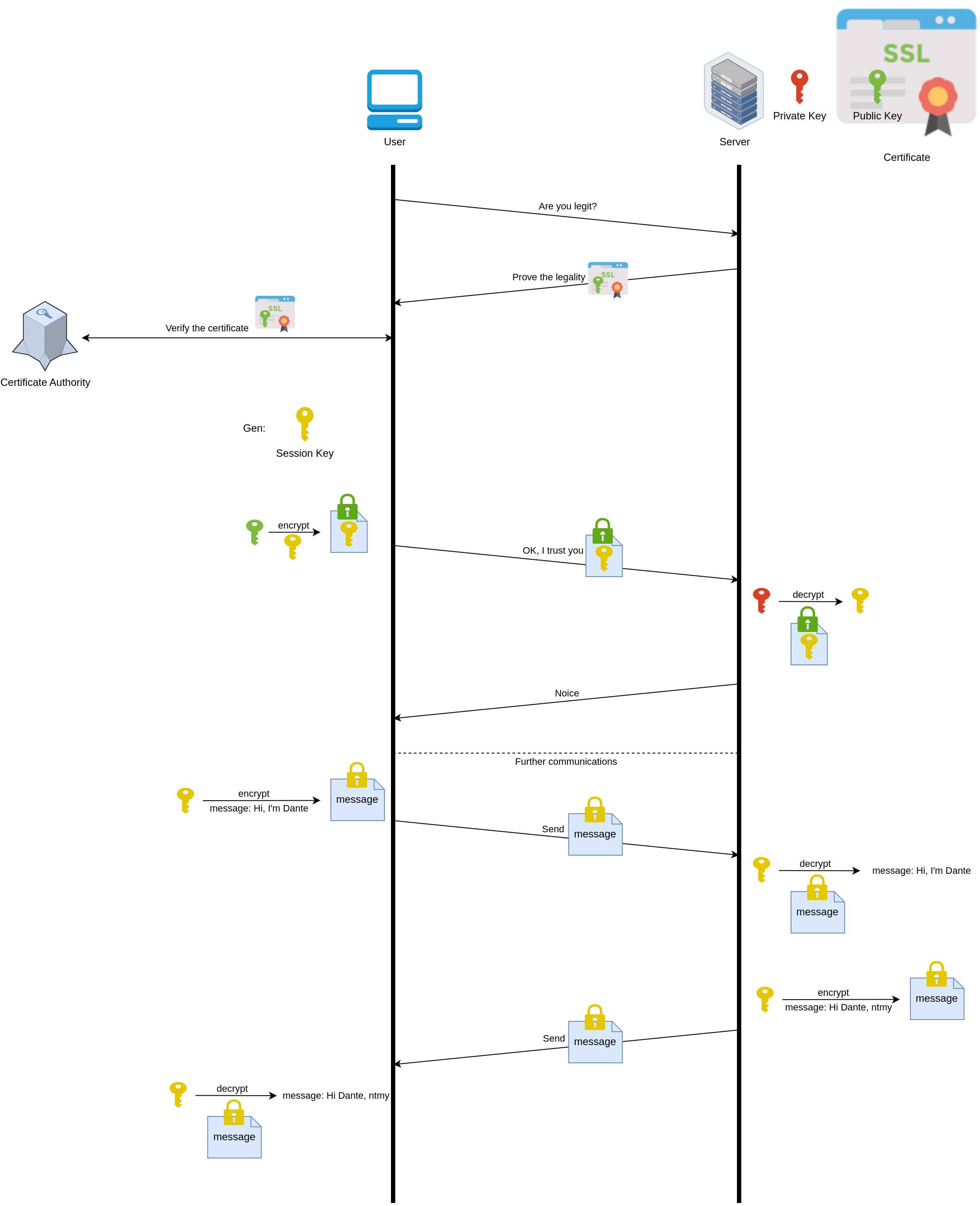
Set up your server using TLS 1.2 #
Nginx
- Open Your Nginx Configuration
sudo vi /etc/nginx/sites-enabled/default
- Update the
ssl_protocolsdirective and configure cipher suites:ssl_protocols TLSv1.2;ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256';- When you set up a free SSL certificate with Certbot (Let’s Encrypt certificate), Certbot automatically sets up
ssl_protocolsandssl_ciphersfor you (include /etc/letsencrypt/options-ssl-nginx.conf;). I commented this out to allow my demo to work correctly
server {
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/mnptt.io.vn/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/mnptt.io.vn/privkey.pem; # managed by Certbot
#include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
# Downgrade to TLS 1.2
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256';
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name mnptt.io.vn;
location / {
try_files $uri $uri/ =404;
}
}
- Test the configuration
sudo nginx -t
- Reload Nginx
sudo systemctl reload nginx
- Verify
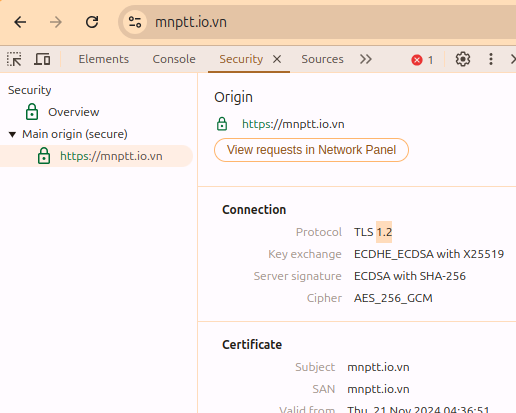
TLS 1.3 #
- Key exchange algorithm: Diffie-Hellman, Elliptic-curve Diffie-Hellman (ECDH)
- Round trip time: 1 RTT
- Compatibility: Supported by newer versions of most browsers
Flow #
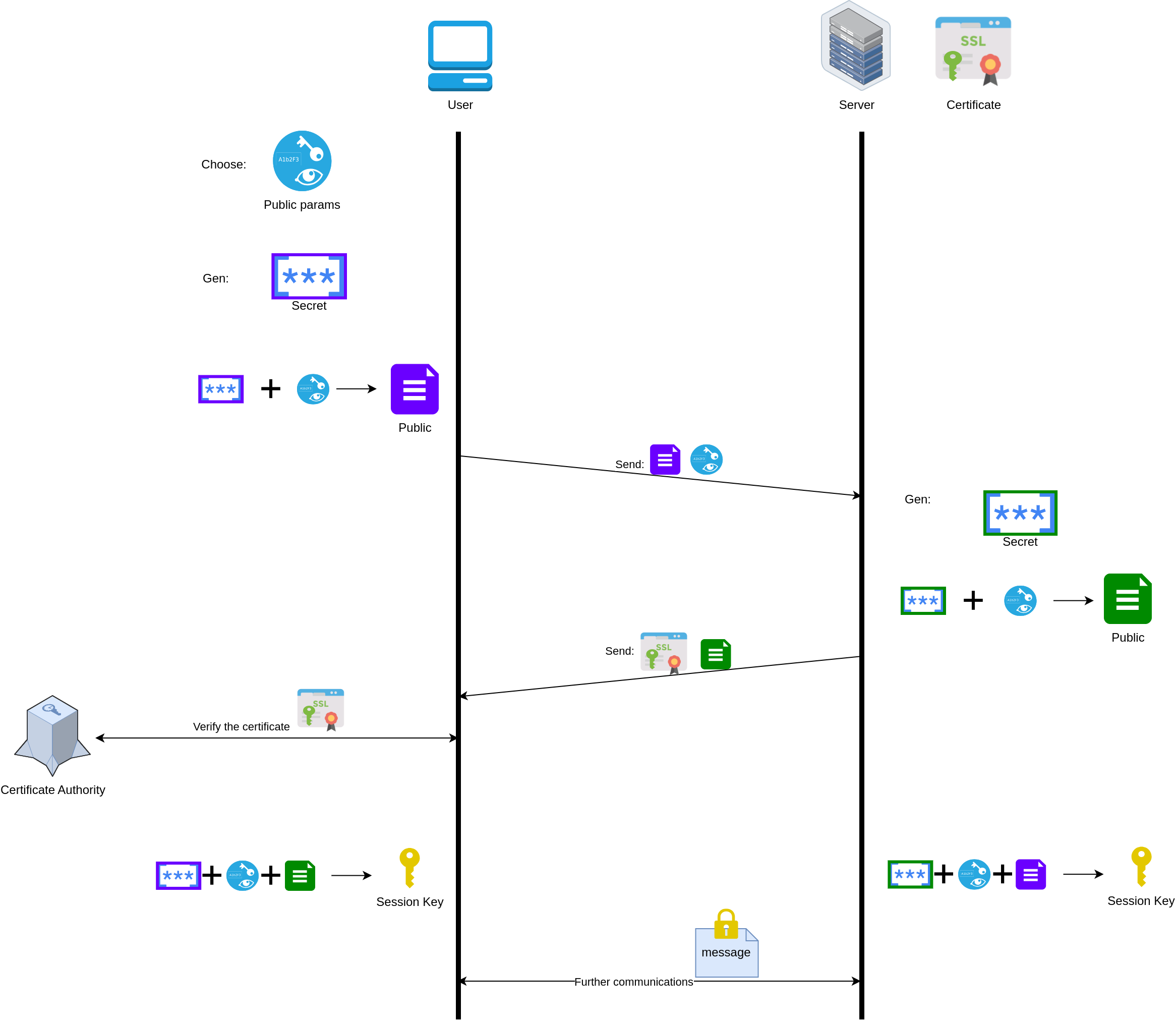
Set up your server using TLS 1.3 #
Nginx
-
Requirements
OpenSSL: 1.1.1 or newerNginx: 1.13.0 or newer
-
Open Your Nginx Configuration
sudo vi /etc/nginx/sites-enabled/default
- Update the
ssl_protocolsdirective and configure cipher suites:ssl_protocols TLSv1.3 TLSv1.2;ssl_ciphers 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384';- When you set up a free SSL certificate with Certbot (Let’s Encrypt certificate), Certbot automatically sets up
ssl_protocolsandssl_ciphersfor you (include /etc/letsencrypt/options-ssl-nginx.conf;). I commented this out to allow my demo to work correctly
server {
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/mnptt.io.vn/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/mnptt.io.vn/privkey.pem; # managed by Certbot
#include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
# Override settings for TLS 1.3
ssl_protocols TLSv1.2 TLSv1.3; # Enable TLS 1.3 and keep TLS 1.2
ssl_ciphers 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384';
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name mnptt.io.vn;
location / {
try_files $uri $uri/ =404;
}
}
- Test the configuration
sudo nginx -t
- Reload Nginx
sudo systemctl reload nginx
- Verify
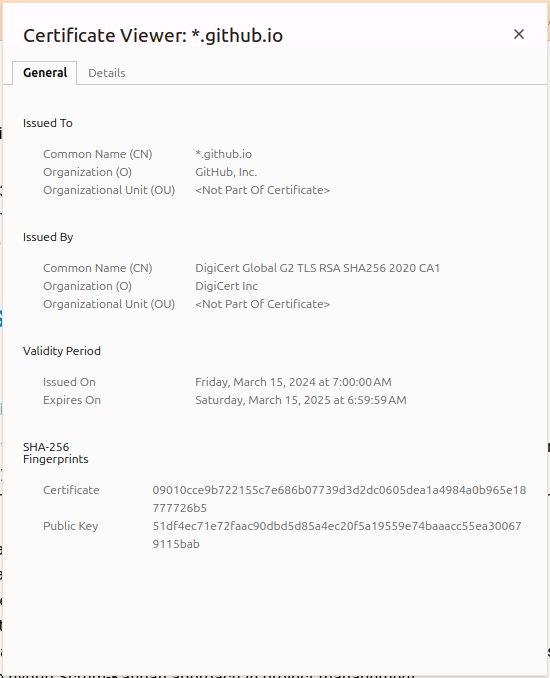
SSL Certificate #
- A SSL certificate contains:
- Domain name it’s issued for
- Certificate Authority (CA)
- Validity period
- Website’s public key
- Other information
Validation levels #
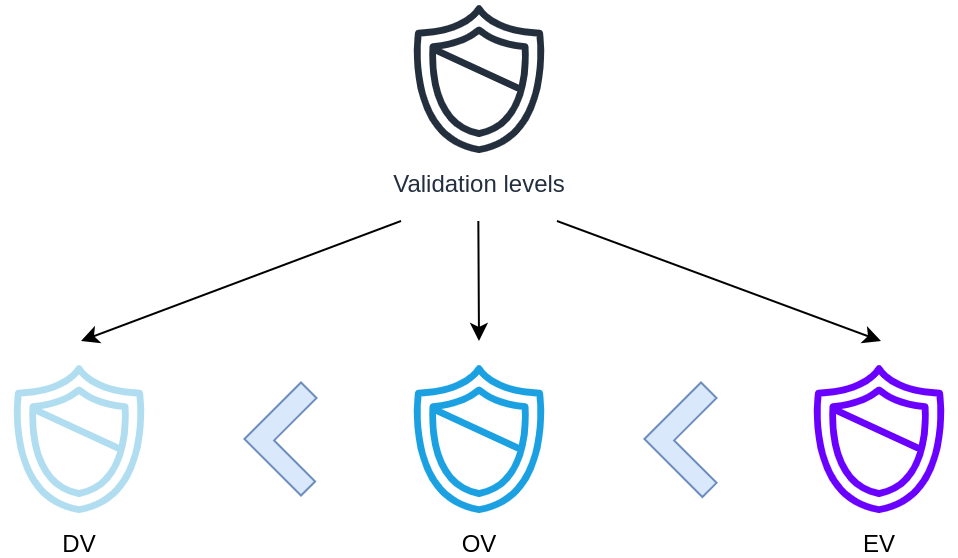
In terms of encryption strength, all three levels provide the same security
Domain Validation #
- Least-stringent level
- User only has to prove they control the domain
- Process can be automated
Organization Validation #
- Manual vetting process
Extended Validation #
- Full background check of the organization
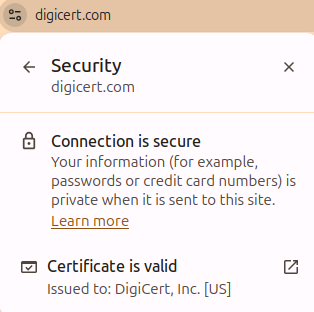
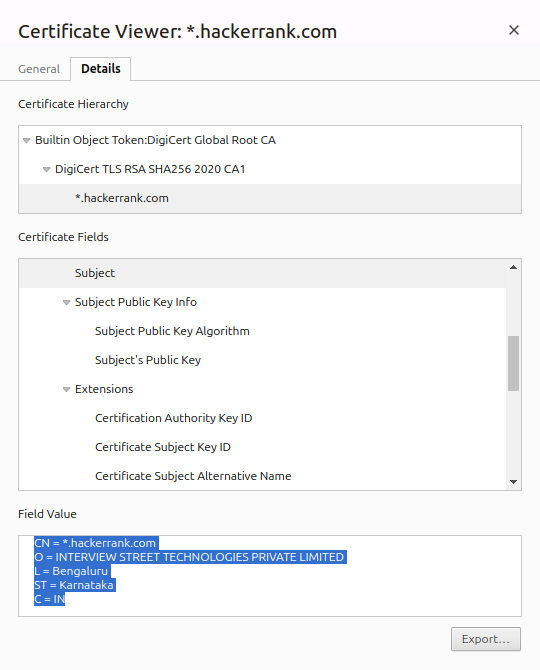
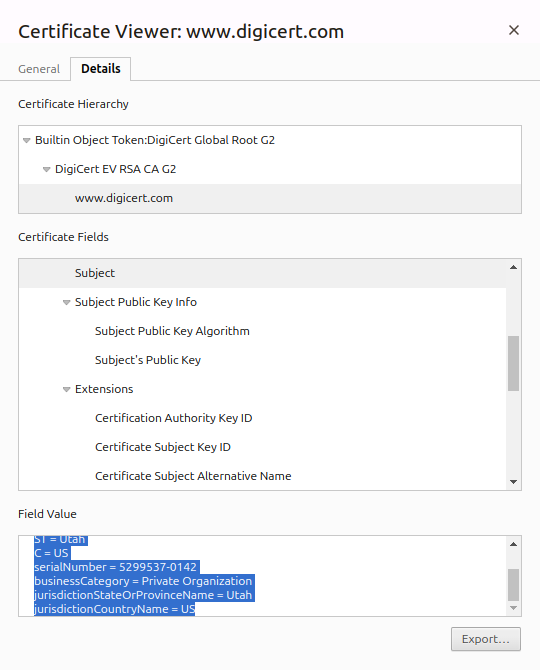
At higher levels, they give more verified information about the website owner’s identity
Types #
Single Domain SSL Certificates #
One domain and all pages

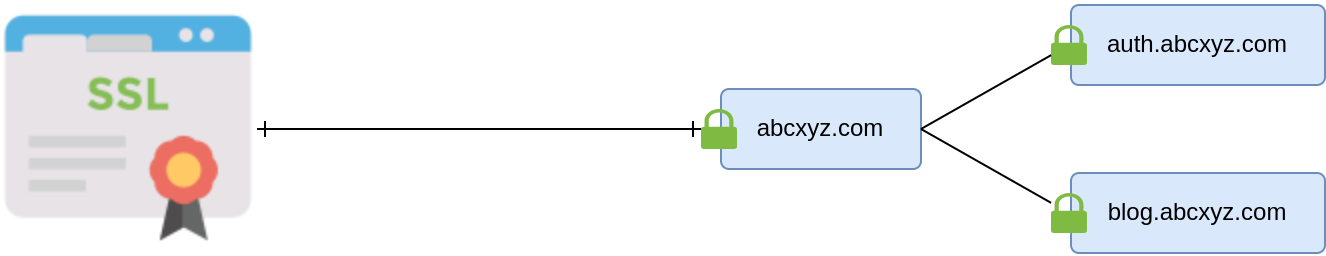
Wildcard SSL Certificates #
One domain and all subdomains
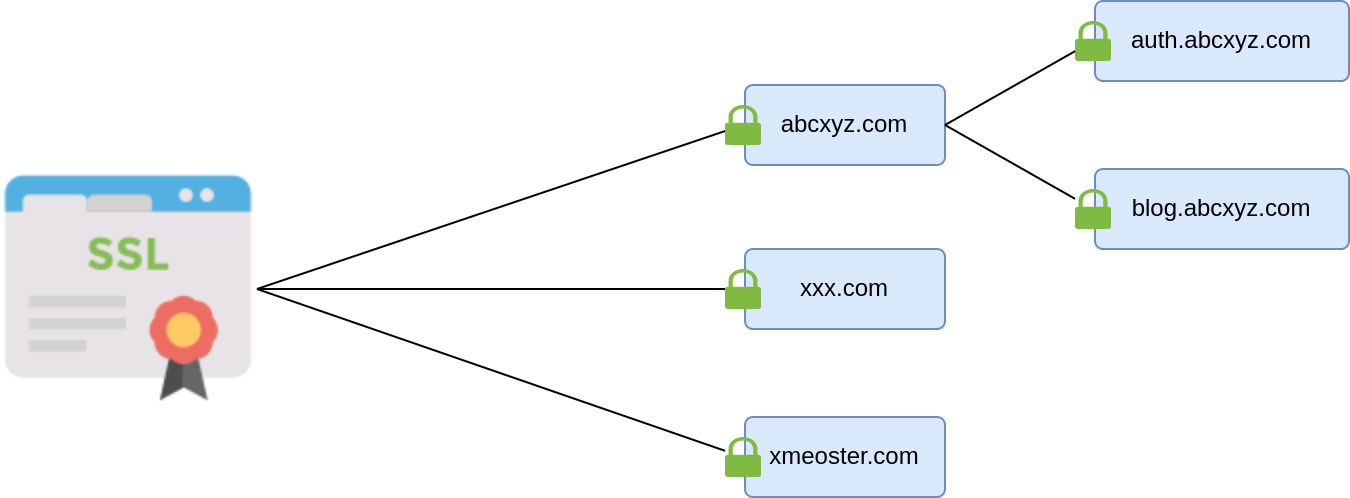
Multi-Domain SSL Certificates #
- It’s a shared certificate
- Multiple distinct domains will be listed on a certificate
How to setup SSL Certificate? #
Reference #
- Cloudflare: How does SSL work?
- Cloudflare: Types of SSL certificates: SSL certificate types explained
- Gigamon: What Is TLS 1.2, and Why Should You (Still) Care?
- Xargs: The Illustrated TLS 1.3 Connection (Nov 13th, 2024)
- Wikipedia: Transport Layer Security (Mar 1st, 2024)
- Cloudflare: A Detailed Look at RFC 8446 (a.k.a. TLS 1.3) (Aug 10th, 2018)
- Youtube: Let’s Encrypt Explained: Free SSL (Oct 25th, 2020)
- Youtube: Are Free SSL Certificates Really Good Enough for Your Website? (Sep 1st, 2022)
- Mozilla: SSL Configuration Generator (Nov 13th, 2024)
- Networkoptix: How to check and/or change the TLS version (Nov 11th, 2024)
Help improve my blog
Was this page helpful to you?
This page was last modified at 2024-01-14